Internet privacy is important, not just for keeping you safe online, but for your mental well-being, say experts.
Reports say that there were 1,862 data breaches in 2021 alone, which is a jump of 68% from 2020. And though you may not realize how scary these numbers are, these breaches can cause consequences ranging from identity theft to physical harm to the victims.
Today, most of us are online and like to share things with the world. And there’s nothing wrong with that. The only problem is, because of the way the online world functions, we end up sharing a lot more than we want to. And this can have dire consequences in the long run.
This is why, in this post, we’ll take an in-depth look at internet privacy, why it matters, and how you can protect yourself online. So, let’s begin.
What is Internet Privacy?
In 2017, CEO and Executive Director of the Stellar Development Foundation, Danielle Dixon, gave a TED talk on Online Privacy. In this talk, she revealed how our online data can trace back to us in the real world.
To confirm her doubts, she set up an experiment and hired an individual to look her up. She gave the individual nothing more than her name, to begin with. And here’s what they found after a few hours of searching.
- Physical addresses for the last 25 years
- Email addresses for the last 25 years
- Where she lives
- Where she intends to live
- What cars she owns
- What cars she drove in the past
- Hundreds of pages of information about her divorce and custody proceedings that contained highly personal information about her and her family
- And they even sent her the latest picture of her son in front of her house.
Even though it seems like we’re browsing the internet in the privacy of our own homes and have control over what we share, the internet is filled with our personal data that can be traced back to our offline lives.
This is why it’s super important to think about internet privacy whenever we go online. And we’ll talk more about how you can do that later in this post.
Is Internet Privacy & Digital Security the Same?
Internet privacy and digital security are closely related, as they both have a significant impact on your cyber safety. Still, there are a few key differences between them.
For example, one difference is that digital privacy concerns the lawful usage, processing, handling, and storing of your personal information. Whereas digital security, or information security, concerns the protection of your data against unauthorized access or malicious attacks.
Take your social media account, for instance. You use an email ID and a password to log in to your account; protecting this information from attacks or exposure is an aspect of digital security. Whereas the way the social media company handles your information is an aspect of internet privacy.
Governments worldwide have set rules for companies to be transparent in their privacy policy and terms and conditions. But when is the last time you took the time to truly read these pages before clicking “I agree”?
Most of us don’t read them—they’re either too long or written in a kind of language that gives us a headache. And that is also where the problem begins.
Concerns Around Internet Privacy
As soon as you click “I Agree,” you give the company permissions like:
Search Engine User Tracking
Search engines like Google and Bing don’t only log what you’re looking for through the search bar, they also track the websites you visit after that. Let’s say you’re using Google Chrome, or logged in to Google from your browser. Technically, you’re in their product. This gives them permission to collect your information, such as:
- Search history
- Web activity
- IP addresses
- Click-through history
Experts say that these data sets can be used for profiling and making a customer persona based on your behavior.
Generally, these customer personas are widely used for personalizing advertisements. But it becomes a serious issue when data-matching algorithms associate your profile with personally identifiable information, which might lead to data breaches.
Data Selling
Even though companies like Facebook, Twitter, and Google don’t sell your data directly, there are companies that do. And it’s not just big tech giants that we’re feeding our data to.
Every website you sign up for, every app you download, every webpage you visit after clicking “I accept” to their cookies request, you’re granting them some rights to your data. And for some of those products and services, those “rights” include selling your data.
There’s literally an industry called the data broker industry that buys personally identifiable information (PII) and behavioral data and sells it to companies.
And though you may trust the companies you’re giving your data to, the internet is a vulnerable space. We can’t say for sure that attackers can’t break the wall and collect your data to use for malicious purposes.
Here’s an example of how vulnerable the internet actually is.
Gamergate
Gamergate is a movement that uses hashtags as an opportunity to harass other people. It started when a guy posted accusations about his ex-girlfriend, who was a game developer.
Harassment campaigns spiraled out of control, both online and offline, against multiple women.
The harassers found personal information like phone numbers and addresses of a huge number of women and posted them online.
This led to several dystopian incidents, all caused by some people hiding behind anonymity and exploiting the vulnerability of the internet.
So, you see, lack of online privacy doesn’t only affect people in the virtual world but in the real world as well. And it can have a significant impact on your mental health, say experts.
Does Siri Record You When It Isn’t On?
In May 2020, The Guardian published an article about Thomas le Bonniec, a whistleblower who revealed how Apple’s virtual assistant “Siri” records and listens to audio without activation.
“I listened to hundreds of recordings every day from various Apple devices (e.g., iPhones, Apple Watches, or iPads). These recordings were often taken outside of any activation of Siri, e.g., in the context of an actual intention from the user to activate it for a request. These processings were made without users being aware of it, and were gathered into datasets to correct the transcription of the recording made by the device,” Bonniec said.
“The recordings were not limited to the users of Apple devices, but also involved relatives, children, friends, colleagues, and whoever could be recorded by the device. The system recorded everything: names, addresses, messages, searches, arguments, background noises, films, and conversations. I heard people talking about their cancer, referring to dead relatives, religion, sexuality, pornography, politics, school, relationships, or drugs with no intention to activate Siri whatsoever.”
After this whistleblowing incident, the company (Apple) published a statement in August saying, “We realize we have not been fully living up to our high ideals.”
Later, they also released a software update that allowed users to opt-in or out of their voice recordings being used to “improve Siri dictation.”
Smartphones are one of people’s most personal possessions. And the thought that yours can start recording whenever it wants is not exactly thrilling. So, if you want to ensure that your privacy is protected, you can opt to turn off Siri and delete the recordings that it has made of you in the past.
Here’s how you do that.
To Turn Off Siri and Delete Stored Recordings
Go to Settings > Scroll to General > Keyboards > Turn off dictation.
You might want to turn dictation off because Apple stores recordings of your voice-to-text messages. Instead of speaking your messages, I recommend taking a moment to type them.
After this:
Go to Settings > Siri & Search > Turn off Listen for “Hey Siri.”
This is probably one of the most important privacy moves you can make. That’s because, once you do this, Apple won’t have any access to your Siri recordings or anything you dictate.
Besides those, also don’t forget to:
Scroll down to Siri and Dictation history > Tap Delete Siri and Dictation History.
You can also turn off all the toggles below that, except “Show When Listening”—leave this on so you’ll know if, by some odd chance, Siri is listening to you.
Airtags: A New Privacy Threat?
Apple AirTags are an easy-to-use tool that can help you reunite with your possessions if you misplace them.
The way they work is simple. Place one of the quarter-sized air tags on your keys, wallet, bag, or anything else you can easily misplace, and you can start tracking it using your phone.

The paired app will tell you the precise location of your personal items, and you can even beep the AirTag to get an auditory confirmation.
Although Apple claims it has paid plenty of attention to privacy, there are certain holes in the product’s security that can make it a significant privacy threat.
How Can AirTags Invade Your Privacy?
A report from the York Regional Police in Canada identified five separate incidents where robbers had slipped AirTags onto high-end vehicles with intentions to steal them.
Their technique was to slip the tracker somewhere onto a target vehicle and then follow its location on their iPhone devices to discover where the cars were parked.
“Since September 2021, officers have investigated five incidents where suspects have placed small tracking devices on high-end vehicles so they can later locate and steal them. Brand name ‘air tags’ are placed in out-of-sight areas of the target vehicles when they are parked in public places like malls or parking lots. Thieves then track the targeted vehicles to the victim’s residence, where they are stolen from the driveway,” says the report.
This is just one story. Another one comes to us from Glendale, Arizona.
Airtag Stalking: The Story of Cindy and Many Others
Teenager Cyndi Miles was going about her evening as usual. She went from a convenience store to a fast-food store, then to her relative’s house.
But when she was in the store, she felt like a man and a woman were stalking her.
Although this was an uneasy experience for miles, she came back home. And what happened several hours later sent a chill through her spine.
She received a message on her iPhone saying an unknown Airtag was following her, leaving her uneasy for days.
“It just made me really scared. Like I didn’t want to leave the house, and I didn’t want to go anywhere, especially at night or by myself,” said Cyndi Miles.
If you search online, you can find a ton of news articles talking about people who were a victim of Airtag stalking, proving that Airtags in the wrong hands can put a massive gap in your privacy.
So, what can you do if you’re being tracked, or how can you prevent these kinds of tracking efforts?
How To Protect Yourself from AirTag Tracking and Stalking
Most Apple devices come with a “Find My” app.
- Go to the app and check for items detected near me.
- Click on any unknown AirTag and click play sound to locate the AirTag.
Check out the video below by Apple to learn more.
Second, look closely for an apple message saying, “An AirTag has been detected traveling with you.” If you receive the message, follow the steps in the video above.
Contact your local law enforcement if you feel your safety is at risk. This way, they can work with Apple to get to the bottom of why this air tag was placed on your belongings.
Internet Privacy & Mental Health: The Link
According to Elias Aboujaoude from Stanford University, privacy mediates vital psychological needs, like the ability to recover from setbacks, achieve catharsis, and have a fresh start. If we’re constantly under a microscope, we may have difficulty meeting these needs.
“Yet this is the state we’re in thanks to social media and companies whose business model is to endlessly mine and sell our personal data,” says Aboujaoude.
“In the popular media, there are hundreds of stories about cyberstalking or revenge explicit materials,” he said, noting that some of his patients have suffered from anxiety, depression, and post-traumatic stress disorder after their personal details were exposed online. “I was struck by how little there has been in the medical literature about this issue.”
Internet privacy is closely linked to our mental health. When we sense that we’re lacking privacy, even online, experts say that it can weigh us down by diminishing the emotional security that comes with privacy. You may not even know this on a conscious level, but subconsciously you’ll be noting its effects.
What Can You Do?
By making a few minor changes to your devices, accounts, and online behaviors, you can protect your privacy from those you don’t consent to share your information with. Here’s a list of a few of those changes.
Secure Your Devices
Hackers use several schemes to steal your personal data, like phishing, malware, and technical hacks (getting into your secure devices through your network). Most of these hacks aren’t obvious at first glance. So, make sure to use antivirus software and applications to secure your devices.
There are many antivirus programs that do much more than search and destroy viruses and malware on your device. They also notify you if the link you’re clicking or the website you’re visiting is malicious.
Do your research, and choose an antivirus that fits you the best.
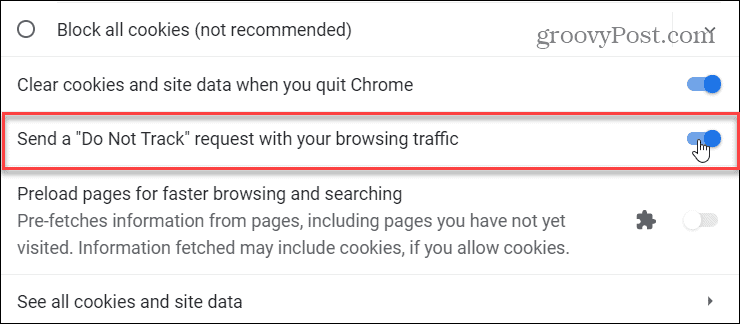
Use the DNT Setting
DNT stands for “Do Not Track,” and it’s a web browser setting that tells your browser to not accept cookies from other websites. By 2011, almost all major browsers have adopted DNT. So, turn it on.
To enable DNT on Chrome:
Click on the three dots at the top right corner of the browser and click Settings.
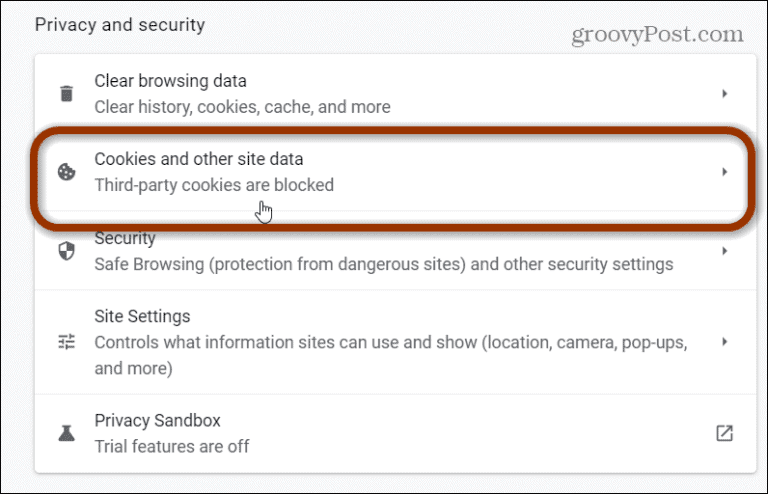
On the Settings page, find the “Privacy and security” section and hit Cookies and other site data.
Then scroll down and switch on the “Send a ‘Do Not Track’ request with your browsing traffic” button.
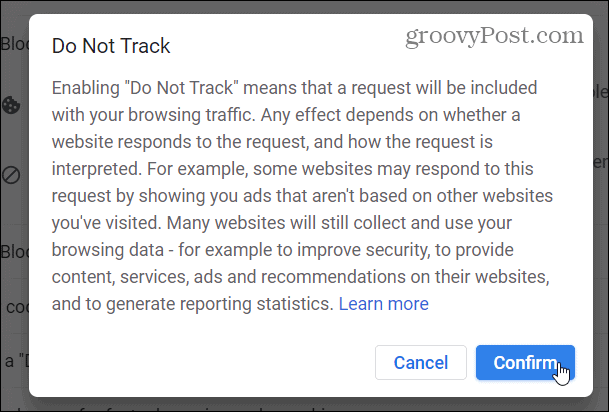
A message explaining DNT will come up on your screen. Carefully read and if it’s okay with you, click Confirm and close the Settings tab.
Opt-Out of App Tracking
You can restrict the applications on your phone from having certain types of access by going to your phone’s settings and turning them off.
While doing this, keep in mind that turning off some permissions—like location data in apps like Google Maps—isn’t optimal. But most apps on the internet ask for more permissions than they require to function. So, at your own discretion, turn off those permissions.
Here’s how to access these settings on Android and iOS.
Android
From support.google.com:
- On your phone, open the Settings app.
- Tap Apps.
- Tap the app you want to change. If you can’t find it, tap See all apps. Then, choose your app.
- Tap Permissions.
- If you allowed or denied any permissions for the app, you’d find them here.
- To change a permission setting, tap it, then choose Allow or Don’t allow.
For location, camera, and microphone permissions, you may be able to choose:
All the time (Location only): The app can use the permission at any time, even when you’re not using the app.
Allow only while using the app: The app can use the permission only when you’re using that app.
Ask every time: Every time you open the app, it’ll ask to use the permission. It can use the permission until you’re done with the app.
Don’t allow: The app cannot use the setting, even when you’re using the app.
iOS
From support.apple.com:
The first time an app wants to use information from another app, you receive a request with an explanation. For example, a messaging app may request access to your contacts to find friends who are using the same app. After you grant or deny access, you can change access later.
- Go to Settings > Privacy.
- Tap a category of information, such as Calendars, Reminders, or Motion & Fitness.
The list shows the apps that requested access. You can turn access on or off for any app on the list.
Review Privacy Policies Carefully
As I already mentioned, most people click “I agree” without reading the privacy policy and terms and conditions documents. I strongly recommend you carefully go through these documents before agreeing to them.
That said, if you don’t have the time, as some of these agreements are dozens of pages long, at least spend some time understanding the kind of information the website or app asks of its users and if you’re comfortable sharing that information.
Use Privacy-Based Browsers & Search Engines
There are many privacy-based browsers and search engines that you can use. For example, instead of using Google Chrome, you can use a browser called Brave.
Brave is a privacy-focused browser that automatically blocks online ads and website cookies in its default settings. And besides making it much safer for you to go online, Brave also makes your browsing almost 3x faster. Because it doesn’t have to load ads and trackers on every website you visit, it can work much faster than Google Chrome.
And instead of using Google as your search engine, you can search with Duck Duck Go. This search engine doesn’t track you at all. This means that each time you search on this engine, it will be like you were never there, meaning no entities can access details of what you’re searching for on the internet.
Be Wary of What You Click Online
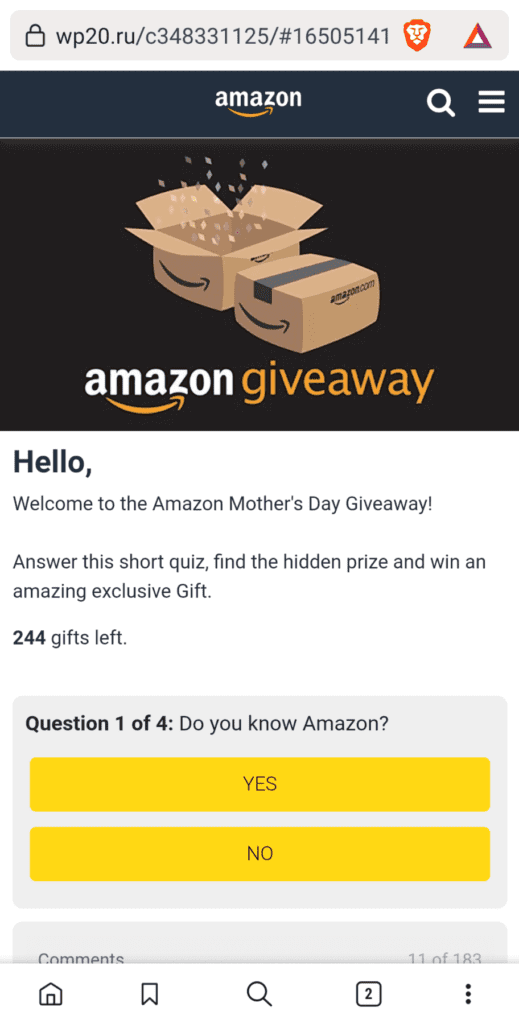
Check out this phishing scam that was in circulation recently.
At first glance, it looks like a legitimate Amazon giveaway. You’ve got your Amazon logo, a website that looks like Amazon, a rush factor saying there are only 244 gifts left. But, if you look at the website URL, it says wp20.ru and not Amazon.com.
What this does is it asks you to complete a simple quiz for a prize and enter your information to be notified of your win. After that, it will ask you to share this with your friends if you want to withdraw your winnings. And just like that, you have voluntarily given your data, and that of your friends, to malicious actors.
Always be wary of what you click online. Start with checking out the URL of the page you’re visiting. Is it legitimate? Are there any spelling mistakes? Does it say http:// instead of https://?
There’s an excellent WikiHow article on this subject called “How to Find if a Website Is Legitimate?”. So, do check it out.
Recycle Your Devices Properly
Data is recoverable. When you delete files from your system, they don’t go away. The device just breaks it down to information that your memory can’t read. When you throw away your old devices after doing a quick format, there’s a high chance that someone can recover everything you deleted on your device within a few hours.
So, always go to a proper tech-waste recycling company to discard your old electronic gadgets instead of throwing them away in the bin.
Final Thoughts
This post, in no way, intends to make you paranoid or scare you into not using technology. Technology is amazing and has a ton of benefits. It’s just that being careful on the internet is the only way to avoid many of the risks that come with exposing yourself online.
Internet privacy has become vital now, more than ever. And now is the time to take it seriously, because technology is evolving and getting more involved in our lives. Soon—especially with developments like the metaverse— we’ll be telling the internet more about ourselves than we’ve ever done before.
Building internet privacy doesn’t mean shutting your gadgets down, closing all your social accounts, and living like humans lived in the 1800s. It just means having some control over what you share and who you share it with.
Having control over how you use your tech is also one of the primary aspects of building a healthier relationship with technology. Check out “The Healthier Tech Podcast” by SYB to learn more about how you can make technology work in your favor, and not vice versa.